
It finally happened. One of your employees clicked on a phishy link and your company is experiencing a data breach. They knew something wasn’t right once they clicked it, but they didn’t know where to turn. They couldn’t remember who to notify or what their next steps should be. So they waited and hoped no one would notice. Maybe it wouldn’t be that big of a deal. That only made things worse.
We understand this scenario is what nightmares are made of. But good news, there’s a simple solution that will help your whole organization respond correctly in times of crisis: policies and procedures. By providing your employees clear guidelines in well defined documentation, you can be confident that your organization is prepared to face today’s threats confidently.
If your organization has yet to implement policies and procedures, we understand how intimidating this project might be. Or maybe you’re just not sure what needs to be included in a policy or the difference between the two documents. Throughout this blog, we’ll examine what policies and procedures are as well as their benefit to your organization.
What Are Policies and Procedures?
In the information security industry, policies and procedures refer to the documentation that describes how your business is run.
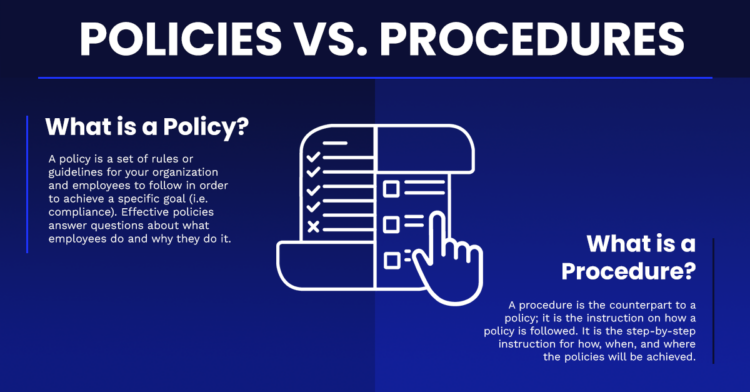
What is a policy?
A policy is a set of rules or guidelines for your organization and employees to follow in order to achieve a specific goal (i.e. compliance). Effective policies answer questions about what employees do (such as directions, limits, principles, and decision-making guidance) and why they do it.
What is a procedure?
A procedure is the counterpart to a policy; it is the instruction on how a policy is followed. It is the step-by-step instruction for how, when, and where the policies outlined above will be achieved. A policy defines a rule, and the procedure defines who is expected to do it and how they are expected to do it.
The main takeaway: a policy defines a rule, and the procedure defines who is expected to do it and how they are expected to do it.
Why Are Documented Policies, Procedures, and Protocols Important?
Many companies reluctantly approach policies and procedures, overlooking their fundamental role. It’s not about conforming to industry best practices or becoming a faceless corporate entity; policies and procedures clarify management’s objectives and the processes involved.
From my experience, the main distinction between a small and medium-sized business doesn’t pertain to revenue or workforce size. Rather, it depends on management investing their time in formulating, implementing, and upholding policies and procedures.
Why are these so critical to company success?
Companies with mature policies, procedures, and systems are easier to audit, have a better understanding of their security posture and risk, and generally just seem to be operating far more sustainably than those who haven’t paid much attention to governance.
3 Reasons Why Companies Avoid Policies and Procedures
Small business’ management generally has the same set of objections to writing down a set of policies and procedures, all relating to difficulty, company culture, and time restraints. But, let’s remember: the benefits outweigh the pain of policies and procedures. Let’s explore the top three reasons why companies may avoid developing policies and procedures.
1. It’s Hard To Write Policies and Procedures
Most companies without mature policies and procedures are operating fairly well otherwise they wouldn’t still be in business. It’s easier to define security from the very beginning, but that doesn’t mean it’s too late if you start later.
Sometimes, the main concern centers on the challenge of putting policies and procedures into writing, but many people are afraid they’ll reveal any mistakes. Start by assessing your current situation, and then take a pragmatic approach to where you want to go. While you may not meet the highest standards in some areas, allowing embarrassment to prevent you from documenting policies is missing the point. Understanding your current practices is essential for identifying real business risks, establishing your future path, creating an accurate budget, and effectively handling unexpected situations
An auditor’s hint: If your practice isn’t “correct,” but you’re honest about it, it’s far less of a problem than if you don’t have anything written down at all.
To learn more about writing company policies and procedures, read How to Write a Privacy Policy (With 3 Sample References) and Writing a Change Management Policy.
2. Policies and Procedures Will Change My Company
Writing everything down, putting your hands on formal processes, and setting expectations force you to sacrifice some flexibility. These extra additions do add a bit of overhead and may result in necessary changes to corporate structure, company culture, revenue pipeline, or “informal, but really good” processes to support the requirements you’ve laid out. Depending on your existing structure, you may even discover you need some additional staff to handle new responsibilities, or some processes might move a bit slower.
For example, with new policies and procedures implemented, your network engineer now needs management to sign off on a firewall change. Your staff may not be able to simply call and get a new permission to some additional part of the network. That’s going to add some time and maybe even a little frustration to the process, right?
Alternatively, how much would you lose if you lost the only employee who understood exactly why your firewall is set up the way it is? Without writing these processes down, you create massive vulnerabilities. People, training, standards, applications – how much is that little bit of overhead worth if it ensures you have a handle on what’s going on inside of your company, your networks, and your enterprise?
You can mitigate the change somewhat by writing your company culture into your policies and procedures. Nowhere is it enforced that policies and procedures must be horribly formal, boring-to-read documents filled with legalese and pain. What makes people want to work there?
Fit your policies and procedures to your company culture, your business, and how your people interact. This will minimize the hardship of implementing them and help preserve what makes your organization unique.
3. There’s No Time to Write Policies and Procedures
This is the most valid argument. In a world of lean staff, fast turnaround, and an emphasis on doing a lot with a little, finding the time for governance may be extremely difficult. However, any management book, essay, or whitepaper, would all agree that if you follow the process, defined policies and procedures will improve your business at every level. You simply can’t pass any formal audit without them. The time to do the work and document your policies and procedures has to be found.
If you can commit to establishing and enforcing your policies, you’ll be shocked at the short-term win in how easy an audit becomes, and even more impressed with the long-term advantages you gain. Your operations will be less stressful, your people will have more direction and, if done well, you’ll finally know exactly what it is you’re managing and why.
Ultimately, it’s clear that while writing and enforcing companywide policies and procedures might seem daunting at first, the benefits far outweigh the concerns. From keeping everyone on the same page to ensuring consistency and compliance, these guidelines are the glue that holds it all together. So, don’t be too quick to dismiss the idea – embrace those policies and procedures and watch your business thrive.
A Note from the Auditor
Throughout my career, I’ve had the fantastic experience of working with small businesses who are new to the idea of being audited.
I’ve seen organizations at every level of readiness, from “We’ve got this, we are prepared,” to, “Why is this so difficult?” It still amazes me that the toughest audits always are a function of the same problem: policies and procedures.
In the world of information security, policies and procedures are better than gold. They are more important than your wireless security keys, more vital than your CEO’s parking spot. They are so important, in fact, that every major information security audit framework has at least one entire section devoted completely to the policies and procedures that underlie your operation.
The PCI DSS audit framework has section 12, the SOC 2 audit framework has governance and compliance as a full quarter of its audit objectives, and HIPAA regulations have an entire subsection devoted to policy.
Partner with KirkpatrickPrice to Create Unstoppable Policies and Procedures
We understand how much it easier said than done it is to implement unstoppable policies and procedures. Our team of experts is ready to walk alongside your business in developing the right policies and procedures for your unique needs. Contact our team at Kirkpatrick Price today to get started! We’d be happy to help you at any stage of the journey: from developing your policies to helping you improve them to auditing them for compliance.
More Policy and Procedure Resources
Style Guide to Creating Good Policies
Style Guide to Writing Good Procedures
Why You Need to Document Your Policies and Procedures
PCI Demystified: Policies, Procedures, and Standards


 Because data is viewed as difficult to understand, a blind trust that data is managed well by people that know better than us has continued to persist. This attitude toward privacy and security has cultivated a culture that allows malicious hackers to thrive and has established a place where security is only considered after the theft occurs. But things are looking up: improvements in protecting data are coming. A focus on cybersecurity that includes holding the owners of data responsible for its protection, improved regulation, and better understanding among the general public have started to transform the space into something far more manageable and comprehensible. Organizations are beginning to understand the true importance of protecting the value of the data that they are collecting, storing, and using. The people behind that data are priceless.
Because data is viewed as difficult to understand, a blind trust that data is managed well by people that know better than us has continued to persist. This attitude toward privacy and security has cultivated a culture that allows malicious hackers to thrive and has established a place where security is only considered after the theft occurs. But things are looking up: improvements in protecting data are coming. A focus on cybersecurity that includes holding the owners of data responsible for its protection, improved regulation, and better understanding among the general public have started to transform the space into something far more manageable and comprehensible. Organizations are beginning to understand the true importance of protecting the value of the data that they are collecting, storing, and using. The people behind that data are priceless.
 Security can be simple, but not when it’s ignored and slapped on at the last minute, when the auditors are on their way. Compliance is a way of existence, something that should be embedded into corporate cultures. Designing secure systems around business needs ensures that compliance and security are not an inconvenience.
Security can be simple, but not when it’s ignored and slapped on at the last minute, when the auditors are on their way. Compliance is a way of existence, something that should be embedded into corporate cultures. Designing secure systems around business needs ensures that compliance and security are not an inconvenience.